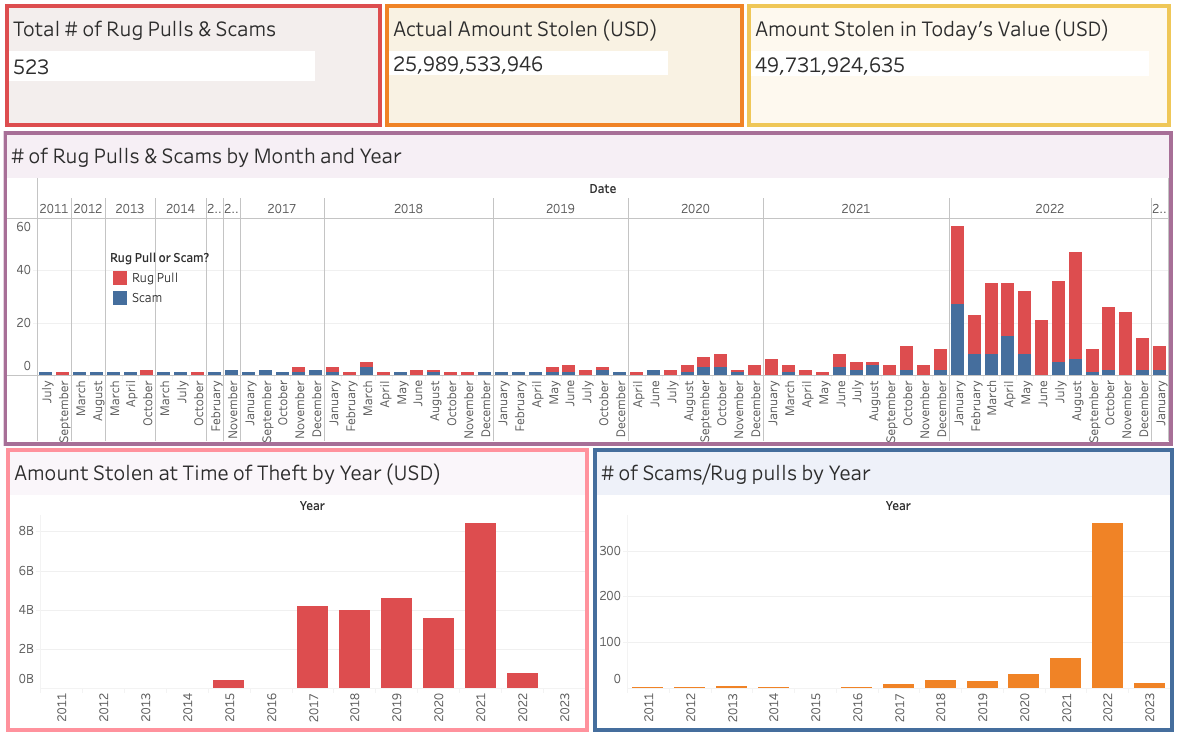
A rug pull is a type of crypto scam that occurs when a team pumps their project’s token before disappearing with the funds, leaving their investors with a valueless asset.
There are three main types of rug pulls in crypto: liquidity stealing, limiting sell orders and dumping.
1.) Liquidity stealing occurs when token creators withdraw all the coins from the liquidity pool. Doing so removes all the value injected into the currency by investors, driving its price down to zero. These “liquidity pulls” usually happen in DeFi environments. A DeFi rug pull is the most common exit scam.
2.) Limiting sell orders is a subtle way for a malicious developer to defraud investors. In this situation, the developer codes the tokens so that they’re the only party that is able to sell them.
3.) Dumping occurs when developers quickly sell off their own large supply of tokens. Doing so drives down the price of the coin and leaves remaining investors holding worthless tokens. “Dumping” usually occurs after heavy promotion on social media platforms. The resulting spike and sell-off are known as a Pump-and-Dump Scheme.